
Blog: Access Control
It’s More Than Getting Through A Door
23 October 2023
Identity Cards – Do They Have The Edge on Biometrics?
It might be difficult to believe, but the use of Biometrics in access control systems is not new and has been around, in one form or another, for nearly fifty years. However, with advancements in technology combined with increased reliability, biometrics are being promoted as a secure and contactless method of entry. As a system they probably are secure and they are contactless, but within a risk based environment that doesn’t mean they are the most appropriate solution. Identity cards have a place that isn’t restricted to getting through a door.
The Technology – A Brief Overview
Biometrics is something physical and unique to an individual, whether it’s their fingerprints, facial features or maybe more intrusively their DNA, which is captured and held on a database. Through a reader which can detect the captured features a comparison is made to the database which, depending on an individual rights, access is granted.
Proximity access control cards, contain encoded information, which if using modern technology based on 13.56MHz, is seen as being secure and difficult to copy. When the card is held close to a reader, it is the card, rather than the individual, that is being identified, with access being granted, if authorised.
Biometrics captures an individual’s personal information
Clearly an individual’s personal characteristics would be difficult to copy, but with Artificial Intelligence perhaps not impossible. However, you can’t lose or forget your biometric credentials and as a technology it can be contactless.
By contrast cards can be lost, stolen or forgotten and with older technology can be cloned, but this is making an assumption about about the cards and the threats that there are. If the cards and associated lanyards do not have any company branding on them and contain minimal information, if lost, it would be difficult to know where it came from. Providing two factor identification ie the card plus a unique PIN, substantially increases the level of protection afforded.
Risk – It’s Not Just About Getting Through A Door
On one level access control systems are about managing access into restricted areas, but this is probably only one control on an identified risk, which in itself might not be owned by Security. The risk could be, for example, the consequences associated with the compromise of sensitive information.
An organisation’s risks are wider than those just owned by Security
The management of that risk and the introduction of controls to mitigate it’s potential compromise are wide. The controls might include the screening of staff or education and training prior to foreign travel, but it is not unusual for different coloured identity cards, as part of the access control system, to be used. The use of those cards enables data to be captured as set out, as an example, in the graph below.
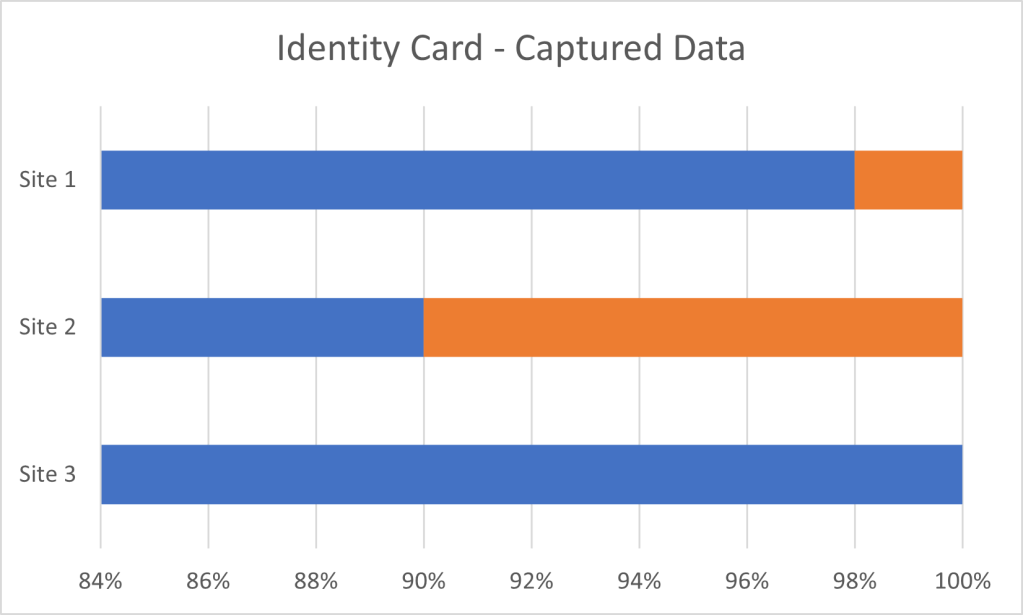
People forgetting, losing or having their Identity Cards stolen, provides a wealth of information to be mined.
What the graph is illustrating is the imaginary data captured across three sites for identity cards that have either been, forgotten, lost or stolen. On any given day, it has to be expected that cards will not be available for any reason, people just do forget them or leave them in the other coat. However and over a period of time, this will lead to an expected daily average, which in the case of Site 1, is 2% of people who haven’t remembered their card. This is seen as a benchmark and from which other sites can be measured.
Risk management requires accurate and ongoing data analysis
Information from Site 2 would suggest that 10% of cards are not available, while on Site 3 there is 100% compliance. But clearly if the benchmark is 2%, it would suggest that on Site 2 there is an issue that would have to be explored and even though Site 3 records 0% issues that in itself is an anomaly that would require investigation.
Further analysis of the data, across all three sites, will reveal not only if it is the same individuals concerned, but if it is peculiar to certain groups of people or predominantly a department. It is the analysis of that data which provides leading indicators that have to be followed up as it might suggest deeper issues than a forgotten identity card.
This is important information that is needed to ensure that a control, introduced to mitigate a risk, is not only working as expected but through analysis, allows wider issues to be addressed. If there is a reliance on biometrics, it raises a question on how that level of information and subsequent analysis would be replaced.
Identity Cards – Do They Have The Edge?
It depends! Security systems are not infallible and certainly not the component parts of it, whether that is identity cards or biometrics. What is perhaps more critical is understanding and managing the potential weaknesses there are and to use that to capture useful data.
The use of a biometric solution at a front entrance might restrict entry at the main door, but personal information has to be captured in doing so. It’s introduction might in itself generate further risks, such as staff resistance that would have to be explored and mitigated. Why should someone give up their finger prints or retinal pattern just to get into a building?
Other than someone’s image, identity cards don’t usually capture personal details and while they can be lost, stolen or swapped, those are weaknesses that are known about. With instructions those weaknesses can be managed and subsequent information, as shown above, analysed to provided leading indicators not just about access control but more deeply.
So do identity cards have the edge? That is a question that can only be answered by understanding the risk!
The decision to use biometrics or identity cards has to be based on the spectrum of risks that there are.
RedLeaf Consultancy – Advising Clients
RedLeaf Consultancy is a consultancy which is primarily concerned with advising clients on how security might impact on the risks that they have have and from that generating solutions.

For more information on RedLeaf Consultancy and our approach to Security Risk Management, please click the button below.
RedLeaf Consultancy
Integrating Security – Bringing Transparency
Available to Meet Your Needs
Available to speak to, video conference, email or meet in person, RedLeaf Consultancy is conveniently located in Northern Ireland, to enable travel throughout the UK, Republic of Ireland and via airport hubs, internationally.
To Contact Redleaf Consultancy
Phone: +44 (0) 7720 820023
Proudly powered by WordPress