
Blog: The Insider Threat
Are New Office Designs an Enabler?
23 September 2024
The Insider Threat and Office Design
The insider threat is a perennial problem and perhaps one of the most difficult issues that Security has to deal with. The threat is generated by people who are trusted, have legitimate access to the facilities and information that an organisation has and, as individuals, are incredibly difficult to identify. It is a problem that has been exacerbated not only by Working From Home and Hybrid Working, but by new office designs. Those designs are not a simple rearranging of the desks, but a highly thought out concept endorsed by senior management that can have a negative impact on security.
A Lesson From History – People Never Change
The Cambridge Five and the Portland Spy Ring, might conjure up images of grainy black and white photographs of the 1950’s and early 1960’s, but both groups typify the trusted insider. No one questioned their loyalty, but they stole the most sensitive of information, over a considerable period of time and in doing so, did irreparable damage to the UK and its allies.

Although they were from a different era, the underlying motives for what they did are no different to those people who engage in insider activity now and that is highlighted by having:
- Strong ideological beliefs that run counter to their home country or the organisation that employs them. (Cambridge Five).
- Personal issues that they either can’t or don’t want to overcome, whether that is excessive drinking, taking illegal drugs or an addiction to gambling, all of which needs to be financed. (Harry Houghton – Portland Spy Ring).
- Being under pressure, perhaps from criminal gangs, foreign states or through an intimate relationship. (Ethel Gee – Portland Spy Ring).
- Resentment, for whatever reason, against their employer, perhaps tied up with lack of promotion, being undervalued or in some cases, just doing it because they can and the feeling of power that generates.
The Cambridge and Portland spies were the people of miniature cameras, micro dots and furtive meetings and while they had access to sensitive documents, copying them was not simple, there were no photocopiers, smartphones or computers.
The images are grainy, but how the Insider acquires information and influence has not changed. They do listen in and overhear conversations, take note of what is on display on desks and boards and require privacy to copy information.
The stolen documents had to be individually photographed, page by page, either in the office or by taking them outside, to the Insider’s own home or a safe location. The resultant images had to be either physically given to their handler or concealed in a dead letter box and as this was government classified information being given to a foreign state, there was always the risk that the Security Services might be following them. They weren’t and were only caught due to information given by a number of defectors from the East, otherwise they would probably have continued.
The Covid 19 Effect – Who is Working From Home?
Even prior to Covid-19, technology was changing how and where people could work, but the pandemic drove the issue forward, as lockdowns forced people to pick up their laptops and set up office in their homes. It was a difficult time, however the cyber security issues were overcome and for those largely office based employees and perhaps those who had and maybe still have the greatest access to information, it has changed their working lives.
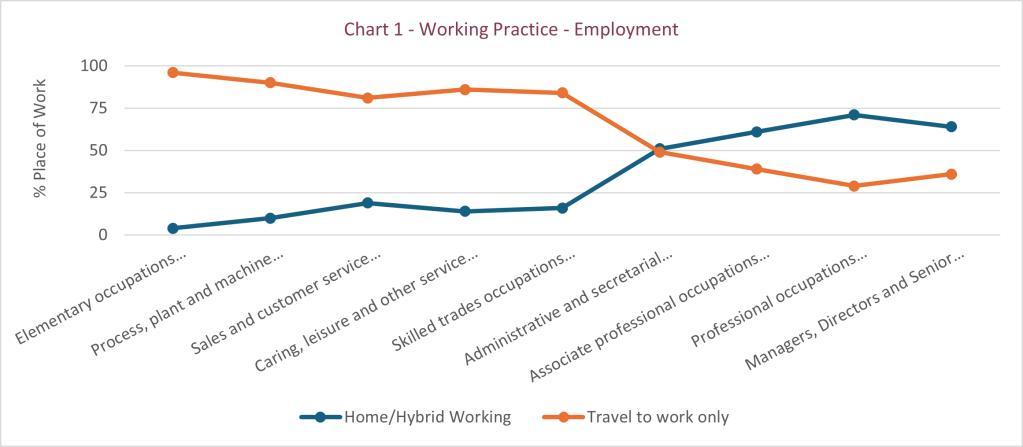
Not everyone has the opportunity to work from home, but some do and this was the subject of a survey, Characteristics of Homeworkers, Great Britain: September 2022 – January 2023, undertaken by the UK Office of National Statistics, (ONS) and published in February 2023. Some of the information from that survey has been collated and is displayed below, Chart 1 – Working Practice – Employment.
What the chart confirms is that it is those people with office based roles and those who work with information, the management of organisations or the generation of ideas, who are more likely to WFH.
Securing Information – Multifaceted and Difficult
Information is not just data held on an IT system or that produced as hard copy documents. It is the thoughts that people have, whether that’s displayed on whiteboards, overheard in conversations, seen on PC screens or, of course, retained in their heads. Securing information is difficult and while controls can be put in place and must be monitored, inevitably it comes down to trust and how that is exploited.
From an Insider Threat perspective open plan offices are difficult to secure, but there is little certainty of security in the home office environment.
The Open Plan Office. Although there might be turnstiles to restrict entry into buildings and cameras to monitor who is entering an office, these are largely measures to control one aspect of the overall risk. Open plan offices are notoriously difficult to secure, there is no restriction of access around a floor, conversations can be overheard, documents can be taken from centralised print rooms or recovered from the confidential waste, but there are reasons why they offer a degree of protection, through:

- Territoriality
- Management overview
- Restricted building access
- Clear desk policies
- Use of identity cards
- Meeting rooms
Working From Home. From an employees perspective, WFH does have personal and what are seen as work advantages as it provides staff with a better work life balance, reduces commuting and other costs, increases autonomy and unlike open plan offices, there is privacy and fewer distractions. While these issues might be true, from a security perspective, there are downsides, which to a large degree are the opposite of the advantages set out above for open plan offices.
- No immediate supervision
- Little confidence that access to information is being restricted
- No restriction on taking images of screens or documents
- Homes are probably less physically secure than offices
- Waste destruction can’t be assured

Within a home working environment, although effective cyber security measures can be put in place, the remainder of the controls necessary to reduce the potential for compromise can’t be, they have been lost.
New Concept – Greater Problems
Post pandemic, with the economic climate that prevailed, compounded by the Great Resignation, employees, who perhaps had the upper hand in employment, saw WFH as a key draw in working for any employer. People wanted and still do want to continue to work from home with resistance to any change.
However, from an organisation’s perspective, the office environment, even when used as part of hybrid working, with staff coming in 2-3 days per week, is seen as having business advantages. The physical contact that people have, rather than via video or telephone calls, does engender greater collaboration, it leads to innovation, allows for mentorship, generates greater camaraderie and team building, all of which are seen as essential in a successful business.
Employers have to draw people into the office and provide them with an experience that meets or is better than WFH and allows those characteristics of collaboration, innovation and positive messages to be engendered. Combined with aspects of WFH, as well as the social aspects of working in cafes, has led to a new workplace design. This is one that does have private individual cubicles for concentration, communal areas to allow for collaboration and sharing of ideas displayed on white boards and interactive walls, as well as no formal team seating arrangements, just turn up and sit down with whoever!


An Insider has value not just because of their direct access to information, but to develop other staff, who may, even unwittingly, provide a wider range of information and influence.
From a security perspective what has been created is an environment that can be exploited by any potential insider. It is clearly one in which conversations with people from across departments can not only be heard but be engaged in and directed. The information displayed on whiteboards or electronic walls can be seen by anyone passing through the area, whether that’s a member of staff, a contractor, a cleaner or security staff, people who don’t need to know.
With no formal seating arrangements, the sense of ownership and territoriality is lost, no single identifiable person who can be held responsible for clear desks or the disposal of confidential waste. From an insider threat perspective the office design has become an enabler in allowing them to more easily acquire information than previously they might have been able to.
The UK National Protective Security Authority stated in a report that the average length of time an Inside Actor was active, before they were caught, was between 6 months and 5 years.
The Role of Security – Managing Risk
The role of Security is to enable an organisation to deliver its objectives through managing the Security Risk and how that might impact, not only on an organisation as whole, but on the individual risks that there are. Those risks however, are probably not owned by Security, but by a range of other departments and individuals across an organisation and this includes the risk of information compromise.
It is through engagement with risk owners that potential impacts can be understood, possible threat actors recognised and the controls necessary to mitigate the risk put in place. Dealing with the Insider Threat should not be seen as a separate or siloed programme, but integral to Security Risk Management, within an overarching risk and governance regime. This is necessary to ensure that those at executive and board level are aware of the potential security issues posed by office designs, together with the immediate and ongoing effect of the controls to mitigate the risk. It is their decision and responsibility on the actions to be taken not that of Security, but they need to know.
Security should be seen as the subject matter expert and understand how the Insider operates. It is their modus operandi, in full, that needs to be appreciated and through discussions and evaluation making risk owners aware of the potential threat.
Need to Know – An Enduring Principle
Need to Know, is probably one of the best known principles within information security and through its application restricts information access to those who need to know it. Without that principle being enforced, maintaining information security is difficult with a much greater likelihood of compromise.
Through the nature of new office designs maintaining the Need to Know principle and countering the issue of the Insider Threat, becomes a lot more challenging.
RedLeaf Consultancy – Advising Clients
RedLeaf Consultancy is a security consultancy that is primarily concerned with advising clients on how security might impact on the risks that they have have and from that generating solutions.
Aidan Anderson of RedLeaf Consultancy brings a depth of experience both in managing the Insider Threat together with undertaking investigations into the threat when it has been realised.

For more information on RedLeaf Consultancy and our approach to Security Risk Management, please click the button below.
RedLeaf Consultancy
Integrating Security – Bringing Transparency
Available to Meet Your Needs
Available to speak to, video conference, email or meet in person, RedLeaf Consultancy is conveniently located in Northern Ireland, to enable travel throughout the UK, Republic of Ireland and via airport hubs, internationally.
To Contact Redleaf Consultancy
Phone: +44 (0) 7720 820023
Proudly powered by WordPress