
Blog: Open Source Intelligence
Its Place Within Security Risk Management
10 June 2024
OSINT – A Product That Has To Be Understood
Open Source Intelligence, OSINT, is not a new concept and has been used by government intelligence agencies and private companies alike for decades. From what was once a closed and specialist market a much wider range of companies are now offering OSINT products. However, as with any other product, its features and benefits, as well as its shortcomings, should be understood, as it can directly impact on Security Risk Management and ultimately the security of an organisation.
In This Blog (Click on the underlined Links)
A Point of Clarity – Information, It’s Not Intelligence and understanding this is key.
OSINT – Where It Begins, a brief overview of OSINT, where it came from and what it can do.
Intelligence – The Compounding of Errors, it’s not unusual to hear of intelligence failures that can have a serious impact on decisions made.
Security – It’s About Managing Risk, OSINT has to feed into the risk equation, if it is wrong, it can distort and perhaps damage, the approach taken.
OSINT – Understanding Compromise, it’s not just the external threats, but how an organisation is increasing its own risk that has to be understood.
The Final Product – It’s More Than OSINT, Security is delivering a consolidated package, with OSINT playing only one part.
OSINT – The Need For Specifications, it is another product that is being bought in that needs to be specified.
A Last Word – It’s Still A Secret, it might be open source, but that doesn’t mean its value to an organisation isn’t Secret.
A Point of Clarity – Information, It’s Not Intelligence
In everyday use, the words Information and Intelligence tend to be interchangeable and largely seen as having the same meaning. However, within OSINT and intelligence more generally, there is a difference that matters.
Information. It’s not uncommon to see incidents represented by digital pins being dropped onto a digital map or the aggregation of data displayed on graphs that illustrate worldwide trends. Although useful, what is being shown is information and while it shouldn’t be dismissed, information is setting out what has happened and what is known about.
Intelligence. By contrast, intelligence is taking information, from a range of sources, analysing it to produce a forecast, with varying degrees of certainty as to what might happen. The objective is to provide a product that enables decisions to be made. Information is what has happened, Intelligence is what might happen.
OSINT – Where It Begins
OSINT has been a feature of intelligence collection efforts for a considerable period of time. As a product, it provided cultural context and insights behind foreign regimes, together with information that may not have been readily available through secret sources. Although the potential sources of information might have been wide and included newspapers, trade magazines, academic papers and foreign language broadcasts, it was a resource intensive activity. There was no machine way of reading information or translating material, everything was manual.
With people, all over the world, uploading images and comments every moment of the day, combined with that produced by businesses, academia, news agencies and governments, the volume of data on the internet is incomprehensible.
The growth of the Internet and in particular Web 2.0 changed the way in which people interacted with it and this generated a seismic shift. The ability not only to read information, but for anyone to upload it onto the Internet, whether that’s individuals through social media sites or academics publishing papers, together with news organisations, businesses and governments, has seen an exponential growth in the volume of data being held in data centres around the world.
The quantity of data held on the Internet is unimaginably large, estimated to be in excess of 140 Zettabytes, but by utilising specialist software tools, that data is searchable and by analysis can produce intelligence. The value of OSINT is seen in Western intelligence services where it is playing an increasingly large part in their intelligence production. In the United States, for example, it is estimated that between 80-90% of all intelligence is OSINT.
Set out in the video below is a simple example of the power of OSINT. What is shown is an image of a rural scene with no identifiable physical features, however as the photograph was taken on a digital device, (in this case an IPhone), it contains metadata. This is information captured and retained with the image and includes the Latitude and Longitude of where the picture was taken and this can be transferred to Google Maps and Google Earth.
What is being demonstrated in the video is the use of Publicly Available Information, (PIA), which is the source used by OSINT. This extends beyond the mapping and imagery shown, into social media sites, news sites, government websites, as the information is freely uploaded and available.
The tools used to extract that information are divided into four general areas, as set out below.
_______________________________________________________________________________________
Linguistic and Text Based
This enables the online search of digitised information, as key words are identified and the summary of large volumes of text enabled, whether that is research papers or social media uploads.
Geospatial
Perhaps what is most associated with this is satellite imagery and the details that can be seen on the ground, whether it’s man made, such as communication networks or port facilities or natural features, including flood plains and weather effects.
Network
This is concerned with identifying relationships between entities, including individuals, groups, as well as their hierarchical status.
Visual Forensics
As shown on the video above, this is concerned with the metadata that is captured with images, but extends to the recognition of “photoshopped” images, as well as the measurement of objects and distances.
_______________________________________________________________________________________
What is being extracted through the use of those tools is information that when processed, as described in the next paragraph, enables an intelligence picture to be produced. Intelligence, however is not infallible and OSINT certainly isn’t.
Intelligence – The Compounding of Errors
The production of Intelligence follows a systematic process that is illustrated by the Intelligence Cycle, shown below. Set across five stages, the objective is to deliver an Intelligence product that meets the decision maker’s requirements. However, errors can occur at each stage of the cycle, which can compound, delivering the wrong answers that can potentially lead to the wrong decisions.
Direction. There has to be a requirement for intelligence that should set out the questions to be answered, the timescales those answers are required within, as well as the funding and authority necessary to achieve those aims. Should the questions not be framed in the right way or just misunderstood, when combined with potentially unrealistic timescales, a lack of funding or authority, the cycle is flawed from the start.
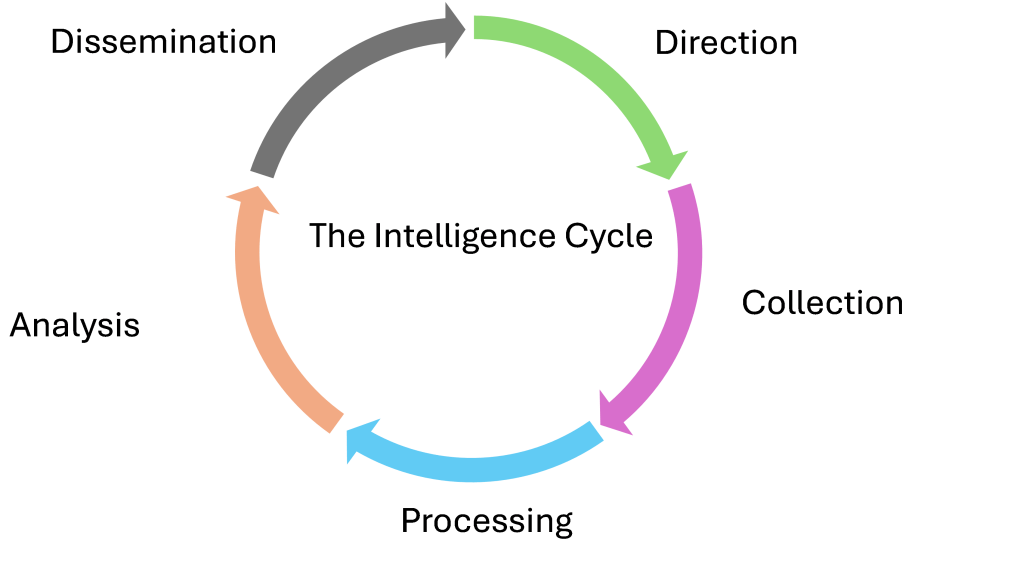
The intelligence cycle is probably one of the most recognisable features in the production of intelligence and while there are other versions, with the emphasis on different stages, the objective is to create a systematic process to generate intelligence.
Collection. The questions established and the methods agreed in the Direction phase, directly impact on the sources used and the depth of information required during the collection process. Clearly when searching the internet the pool of information and the potential sources is going to very large, as is the credibility of the sources and the information they provide. As the volume of data on the internet continues to grow, when combined with the increased use of encryption, makes information increasingly difficult to gather, without continual investment in new software tools.
Translation, it’s more than just words!
Das ist ja sehr tröstlich! This translates from German as:
That‘s very comforting (Google translate), but what it really means is:
Some comfort that is! (Modern German Grammar)
Processing. Once collected, all the information requires to be processed prior to it being made available to the analysts. This is not simply a matter of filing it, what is being built up is the reliability of the sources that have been used, the effect that any bias might have had and the establishing of inter-related information. Bias, whether it’s been introduced through the search algorithms used or even sources such as reputable newspapers, will taint the final product.
Analysis. It is the analysts role to pull together the information, from the range of sources, analyse it and provide an assessment that should answer the original questions posed. Intelligence isn’t a prediction of what will happen, it’s an opinion based on the information available and the skill of the analyst. If the information isn’t there or isn’t reliable or the analyst doesn’t have the requisite skills, this has to be acknowledged and explained.
Dissemination. For OSINT to have any value it has to be disseminated to the relevant individuals, not only in a timely manner, but in the format requested. However, whether that is through verbal briefings, written reports or via software applications, the final product has to answer the initial questions. Dissemination is not a one way process, with analysts expected to answer searching and detailed questions on their reports, making communication skills essential.
The outcome of the Intelligence Cycle, is the delivery of an Intelligence product that should answer the original questions posed. Even if it does, there will be varying degrees of confidence in the veracity of that, normally displayed as a percentage, the higher the percentage, the greater the confidence. However, the product is not an end in itself and is there to enable decisions to be made, it is about managing risk.
Security – It’s About Managing Risk
From the protection of assets, the management of security officers to the installation of CCTV systems, everyone, including security staff, has a view on what security delivers. Although all of those examples are factually correct, what is actually being delivered is Management of the Security Risk, as it impacts on the individual and collective risks that an organisation has. Those risks may not be owned by Security, but by other departments and individuals and could be set at a Strategic, Operational or Tactical level.
The illustration below is taken from ISO 31000 Risk Management and sets out the process by which Risks are identified and ultimately mitigated. It is through the analysis and evaluation process that potential treatment options are established and which ultimately brings the risks within an organisation’s risk appetite.

A common factor throughout the process, is the effect that Threat Actors might have and this reflects the way in which the Risks are to be treated. The evaluation of Threat Actors, taken in their widest sense and including PESTLE analysis, benefits from OSINT, but only if potential errors within the Intelligence Cycle are recognised and negated. This is not just at the initial evaluation stage, but throughout the life of individual and collective risks, as they are monitored and reviewed. If this is not undertaken correctly or if the OSINT being used is impaired, it could skew the assessment and negatively impact on the organisation.
Using OSINT to provide early warning of protest activity is a relatively simple process. A much greater value is gained by understanding an organisation and through strategic OSINT, why, through its actions, it might become a protest group target.
OSINT is often described as providing “Actionable Intelligence”, but this term gives the impression that it is for immediate and short term use. Although there can be value in that, intelligence and its use within Security Risk Management has to be set at different levels, to meet the decision makers requirements, whether at a Strategic, Operational or Tactical level. After all the needs of the board, with the longer term and global view that they take is different than the near term issues at a tactical level.
OSINT – Understanding Compromise
OSINT is often characterised as the identification of Threat Actors, who may wish to cause harm to an organisation, however it is equally important to understand how an organisation might be causing damage to itself. That could be seen through other organisations or countries developing similar products, giving away to much information at conferences or through published papers, the identification of compromised suppliers or the use of drone footage that markets an organisation, but provides an overview of a facilities security. OSINT can reflect back on an organisation to provide early warning of potential compromise and allow counter compromise actions to be taken.
The Final Product – It’s More Than OSINT
Although Intelligence can be delivered as a standalone product, for others to act on, the role of Security is to manage the Security Risk, not just to provide intelligence. A composite view has to be taken that brings together a range of other data, which when centrally collected, collated and analysed, provides a much sharper picture on how security is impacting, either positively or negatively, on an organisation’s risks.

OSINT is only one part of an assessment on the impact that security has on identified risks. It is a process that is undertaken by analysing a wide spread of information and ultimately delivering the product needed.
OSINT, particularly if provided by an external company, may not have access to all sources of information, some of which are set out in the illustration above and most of which are internal to an organisation. It is this consolidated information, that enables a complete Security Risk Management product to be delivered to individual risk owners and which is tailored meets their needs, no matter what level they are sitting at.
OSINT – The Need For Specifications
The seemingly unstoppable growth of information on the internet, when combined with the development of sophisticated software tools, set to exploit it, will continue to expand the commercial availability of OSINT. This can be seen in the drive by government intelligence services, who are increasingly using it as a valuable source and there is no reason to assume that private companies will not follow suit.
However, the capability of any commercial company to provide an OSINT product, is not just dependent on sophisticated software tools, it is wrapped up in the entire Intelligence Cycle. The compounding of issues, whether that is through misunderstanding the original intelligence requirements or analysts not having the necessary training, aptitude and experience to exploit it, might lead to an unquantifiable degree of inaccuracy being fed into the Security Risk Management process, with the resultant detrimental effect that could have.
Whether OSINT is being used to inform decisions on protest group activity or assisting organisations entering new markets, it is essential that detailed specifications are drafted. This extends beyond the product that is to be delivered, but should combine the expectations and requirements of the organisation providing it.
A Last Word – It’s Still A Secret
OSINT may be the result of searching publicly available information on the Internet, but the value and purpose that it has could still be Secret to the organisation concerned. This has to be kept in mind and reflected in security policies, whether OSINT is be bought in from a commercial organisation or if that role is undertaken by an inhouse team.
RedLeaf Consultancy – Advising Clients
RedLeaf Consultancy is a consultancy which is primarily concerned with advising clients on how security might impact on the risks that they have have and from that generating solutions.

For more information on RedLeaf Consultancy and our approach to Security Risk Management, please click the button below.
RedLeaf Consultancy
Integrating Security – Bringing Transparency
Available to Meet Your Needs
Available to speak to, video conference, email or meet in person, RedLeaf Consultancy is conveniently located in Northern Ireland, to enable travel throughout the UK, Republic of Ireland and via airport hubs, internationally.
To Contact Redleaf Consultancy
Phone: +44 (0) 7720 820023
Proudly powered by WordPress